Summary created by Smart Answers AI
In summary:
- Macworld explains how to identify if your Mac has been compromised, covering key warning signs like overheating, browser hijacks, unknown apps, and excessive CPU usage in Activity Monitor.
- Mac users need this knowledge since Macs can be hacked through malware, spyware, ransomware, and port exploits, despite common beliefs about their immunity.
- Essential steps include disconnecting Wi-Fi, checking system settings for suspicious accounts, running antivirus scans, and updating macOS immediately. Detailed instructions are provided below.
It’s a long-held belief of Mac users that their computers are immune to the kind of malware and viruses that plague Windows PCs. While there is some credibility in this idea, we shouldn’t get over-confident when it comes to Mac security, as there are exploits that criminals can use to hack your Mac and leave it like a wide-open door through which they can steal your data or worse.
In this article, we take a look at whether Macs can be hacked, how to tell if your Mac has been hacked or if someone is spying on your Mac, and what you can do if your Mac is being remotely accessed. Here’s what you need to know – and what you need to do.
Signs your Mac has been hacked: At a glance symptom checklist
First some reassurance: you probably haven’t been hacked. It’s more likely that you are dealing with buggy macOS behavior or app related problems. Unfortunately sometimes a macOS update can cause your Mac to start behaving in a strange way, Spotlight indexing, or a kernal-task related to temperature control can cause high CPU usage, as we have found on many occasions.
But sometimes the behaviour really is suspicious. The things to look out for include:
- Mac running really hot, very slow, and the fans very loud when idle.
- Browser-based hijacks, a change to your usual Home Page, redirects, extensions you didn’t install, and suspicious pop-ups – especially if they say ‘Your Mac is infected’.
- Apps you didn’t install, or don’t remember installing.
- Excessive use of CPU in Activity Monitor.
If none of the above apply, your Mac is unlikely to have been hacked. If you are still concerned, read on for details of how to run the checks to confirm whether your Mac has been hacked.
PROMOTION
Protect Your Mac: Intego Mac Premium Bundle
Intego Mac Internet Security X9 offers a useful set of security utilities that help keep your Mac safe and running smoothly and its user-friendly interface is right at home with Apple’s macOS aesthetic. It’s Macworld’s Editors Choice.
Now $29.99 (down from $84.99) for the first year.
What to do if your Mac has been hacked
If you are convinced you have been hacked, then we recommend you do the following:
- Disconnect Wi-Fi.
- Change important passwords using a different device – including your Apple ID.
- Look for any unknown devices associated with your Apple ID and remove any that are suspicious.
- Check for unknown admin accounts, login items, remote access settings, and configuration profiles (we offer details on how to do this below).
- Backup your files carefully (you don’t want your backup to be infected with malware).
- Run a Mac antivirus.
- Update macOS if there are any macOS updates that should be applied.
- Run a clean install of macOS if you are sure you were compromised.
- Enable FileVault and Firewall on your Mac if it’s not already turned on.

Dominik Tomaszewski / Foundry
How to tell if Mac is hacked
If you think your Mac has been hacked there are a few ways to find out. First, look for the signs: Has your Mac slowed down? Is your web connection painfully slow? Do the ads you are seeing look a bit more dodgy than usual? Have you noticed anything strange on your bank statements?
If you fear your Mac may have been hacked, here are some quick things you can do to check for signs your Mac has been compromised:
Check System Settings
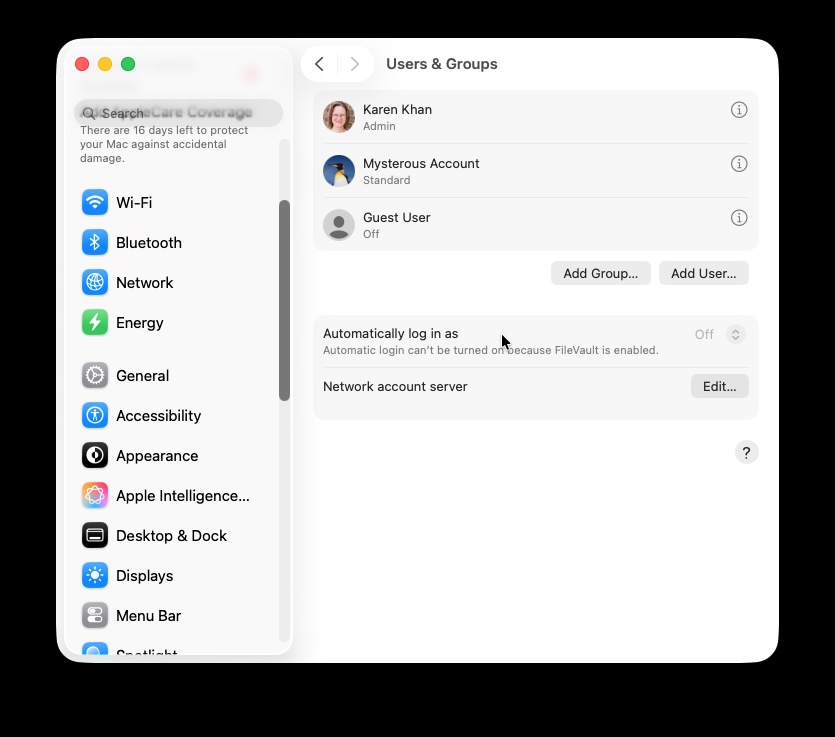
Check to see if a new admin account has appeared.
Foundry
In System Settings you can look for signs that your Mac has been accessed by someone other than yourself.
- Open System Settings.
- Go to Users & Groups to see if a new admin account has been added.
- Make sure your own account type hasn’t changed.
- Look for unknown login item in System Settings > General > Login Items & Extensions. Are there any apps set to launch at startup that you didn’t install?
- Are there any suspicious apps that have been given permission for App Background Activity that you were unaware of?
- Check for any extensions you don’t remember installing in the Extension section.
- Go to System Settings > Privacy & Security and check Remote Desktop to see if any applications have requested access. Look our for unexpected screen sharing or remote access enabled. Check your remote access settings.
- In Privacy & Security check to see if anything has been granted Full Disk Access.
- Also in Privacy & Security check for any Profiles that you didn’t install (you may not see anything, which is nothing to worry about).
- Go to System Settings > General > Sharing and check Screen Sharing, Remote Login, Remote Management and File Sharing to see if they have been enabled without your knowledge.
Check Activity Monitor
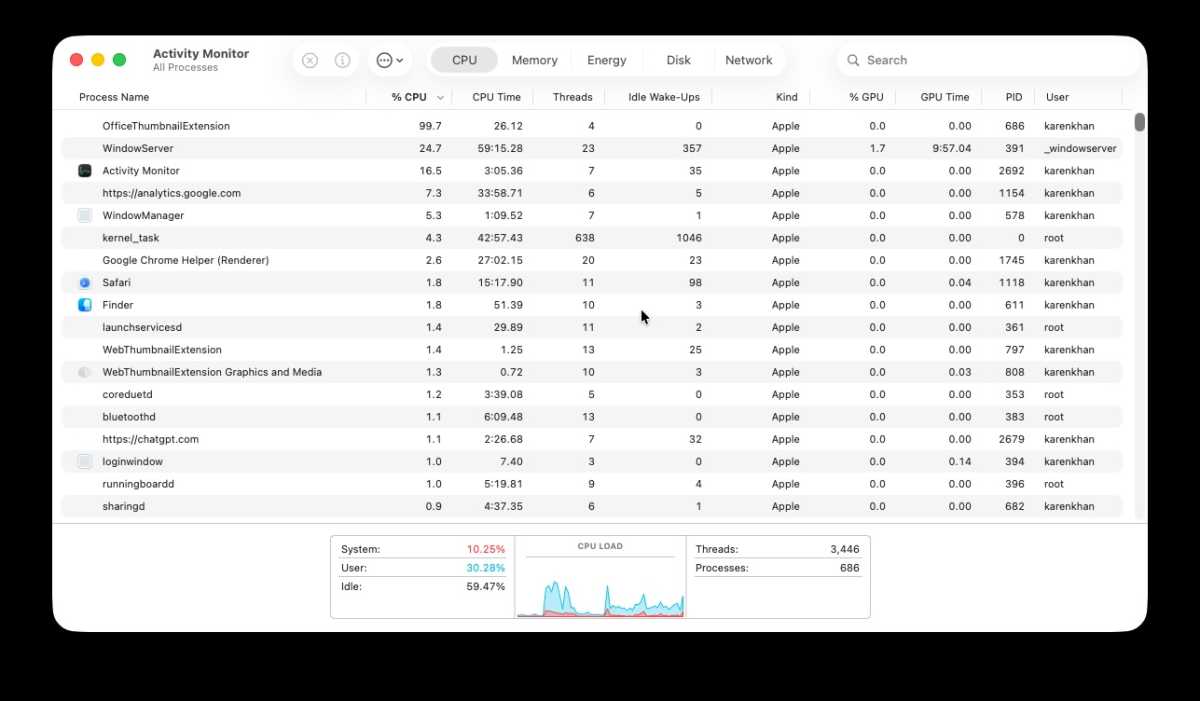
We checked: OfficeThumbnailExtension relates to QuickLook on the Mac and doesn’t seem to be malicious, just annoying!
Foundry
Activity monitor is a great way to check for errant processes that are running on your Mac. One of these processes may be what is causing the symptoms that have made you concerned about your Mac, although it doesn’t necessarily mean you have been compromised.
- To check for suspicious processes running on your Mac open Activity Monitor.
- Click on View > All Processes.
- Click on the CPU tab.
- Sort by % CPU.
- Note any apps or processes using more than 50% of your CPU while your Mac is idle. High CPUs are normally associated with browsers, video apps and games, anything else would be unusual.
- Look for any apps or processes you don’t recognise
- If you see something that looks suspicious Google the process name (but it’s probably nothing to worry about and may be vital for your Mac).
- Next, click on the Network tab.
- Sort by sent bytes.
- Note anything that is sending large amounts of data when you are not uploading anything. Be suspicious of anything sending large amounts of data out, but Google unknown process names before deleting/quitting any processes.
- Now check Memory usage in Activity Monitor by clicking on the Memory tab.
- Look out for apps consuming a lot of RAM.
- Look for evidence of remote access, e.g. processes like: screensharingd, ARDAgent, sshd, remoted, and tools like TeamViewer.
Look for suspicious apps
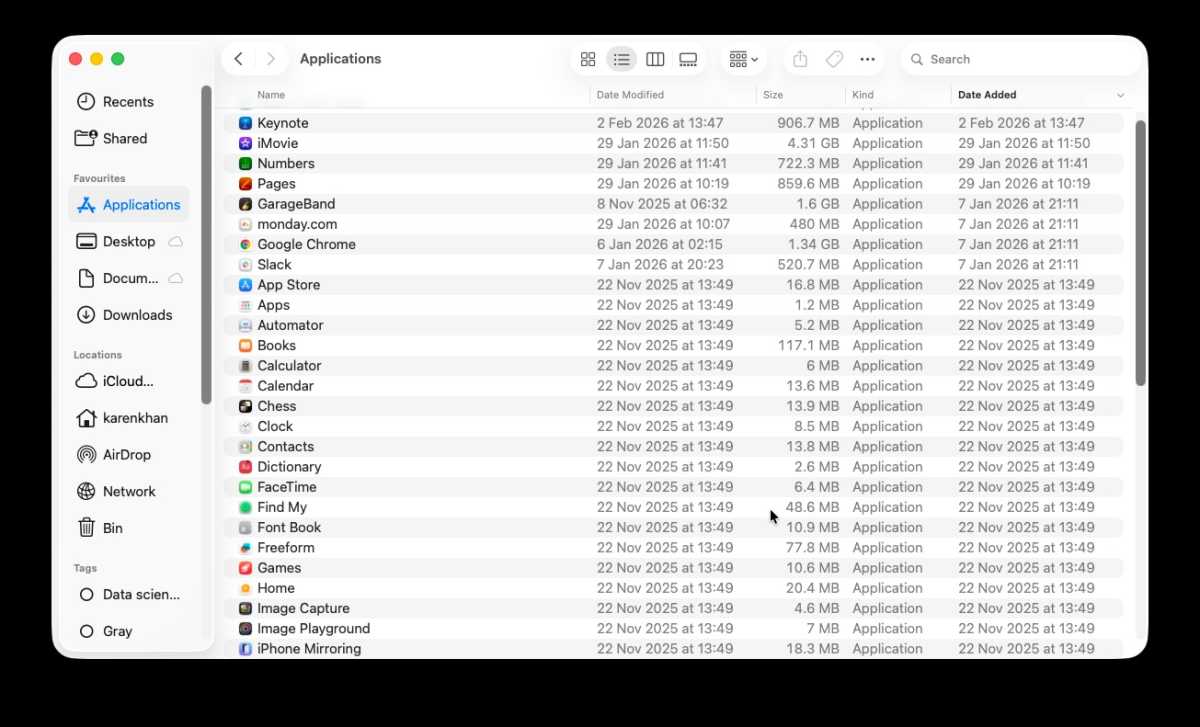
Nothing suspicious looking, but beware of duplicate apps that could be spoofs.
Foundry
Have a look for any apps you don’t remember installing.
- Open the Finder.
- Go to the Applications folder.
- Sort by Date Added (if this isn’t an option right click on the bar and choose Date Added).
- Look for any apps you don’t recognise or don’t remember installing.
Check Browser Extensions
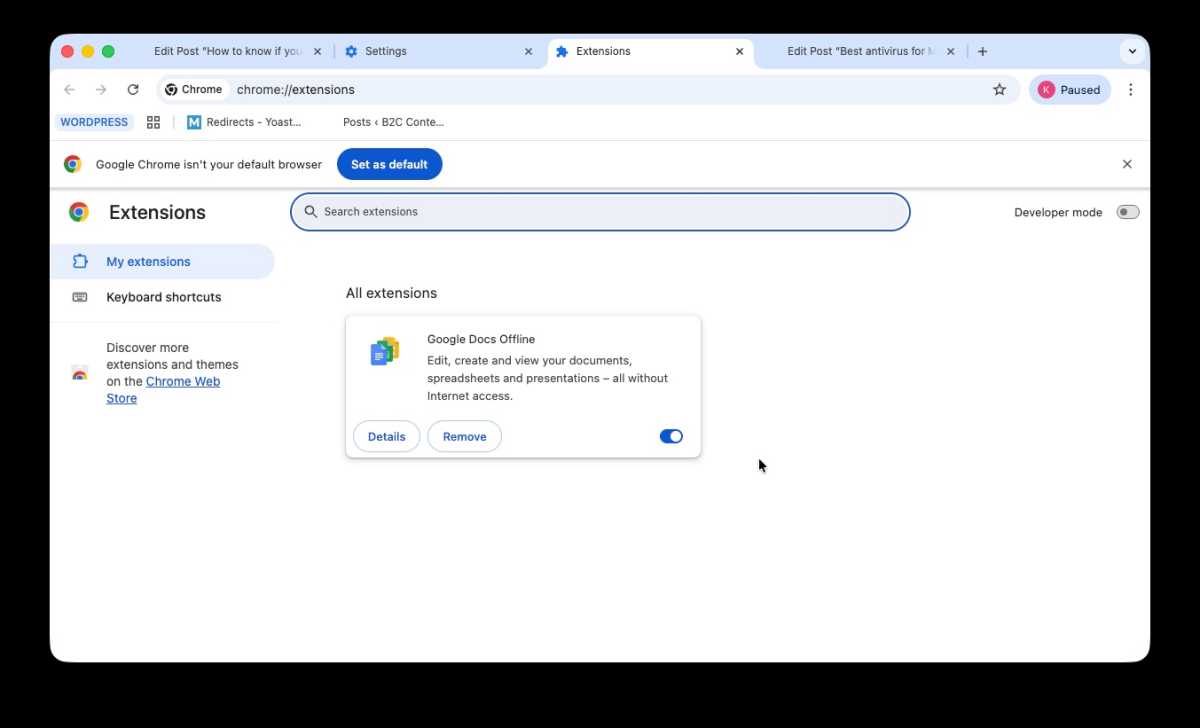
Check Chrome and Safari to see if there are any Extensions you don’t remember installing.
Foundry
Browser hijacks are possible even if your whole system isn’t hacked, so be sure to check Safari, Chrome, FireFox and any other browser you use.
- Look for extensions you don’t remember installing, and delete them.
- In Safari click on Safari > Extensions.
- In Crome click on Chrome > Settings > Extensions.
Scan your Mac with an antivirus solution
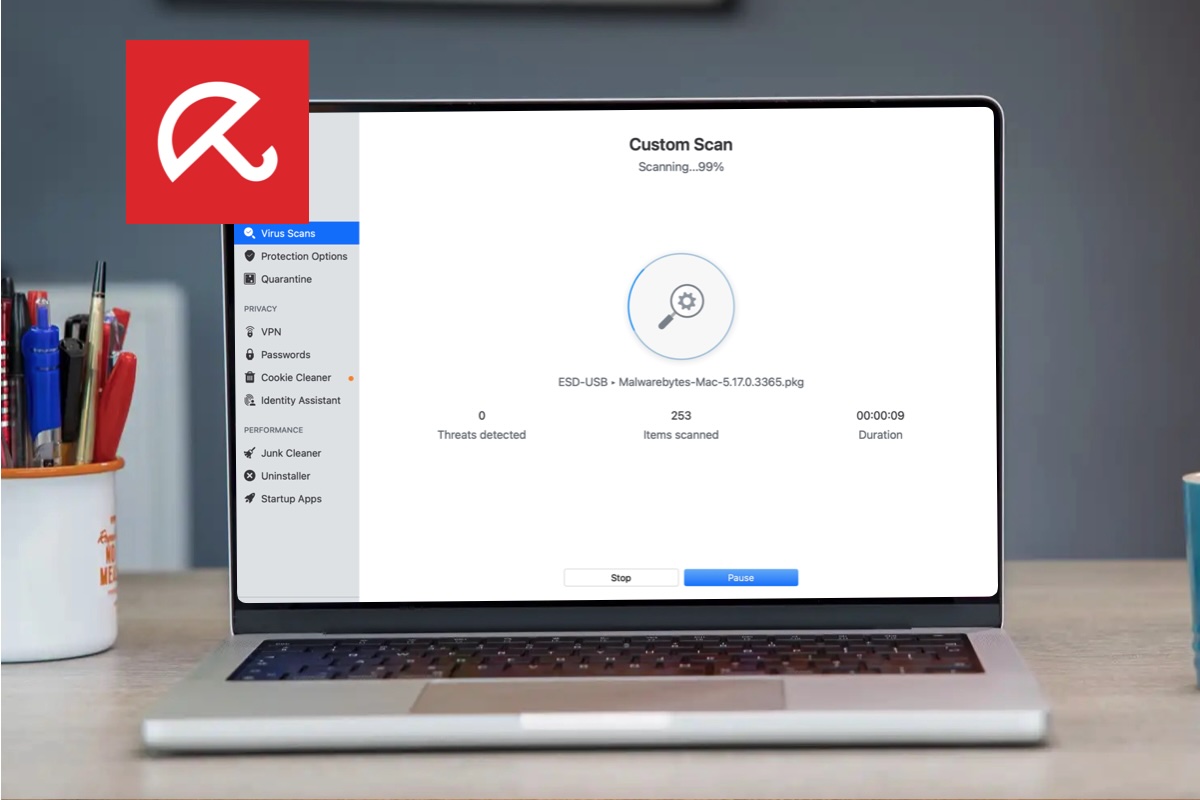
Run a Mac Antivirus solution and scan to see if there is any malware on your Mac.
Foundry
macOS will automatically scan your Mac for any malware definitions that features in XProtect, but you can’t force it to do this. Therefore we strongly recommend that you run a Mac virus scan using a third party security app.
Initiating a virus scan is an easy process that usually begins with the user clicking a Scan or Smart Scan button.
There are various Mac Antivirus apps we recommend, our top choice for Mac users being Intego, but there are lots of options, including some free Antivirus apps. See: Best Mac Antivirus software for the best options.
You may also like to read our guide on how to remove a virus from a Mac.
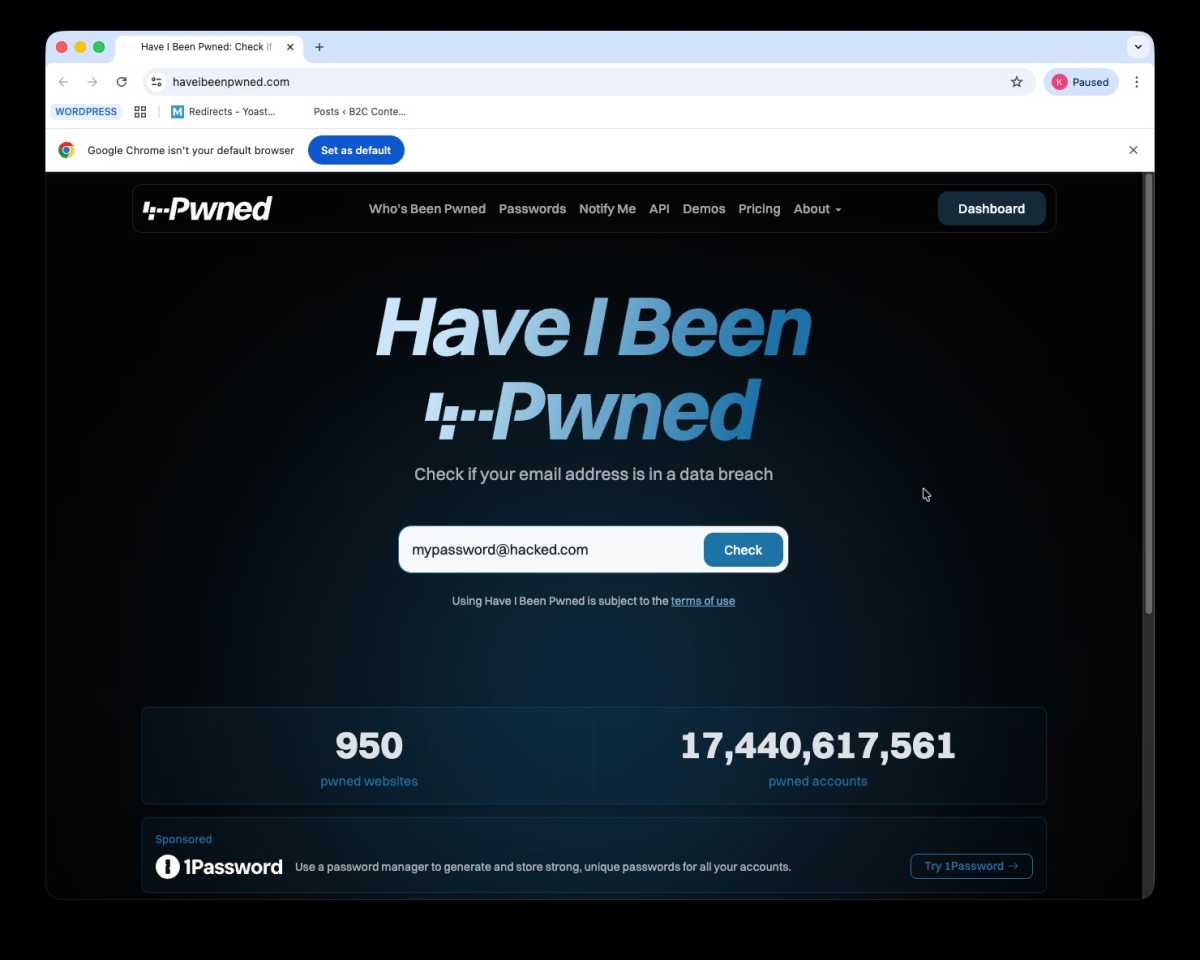
Check your password
Screenshot
Foundry
If you think an account might have been hacked then check the website haveibeenpwned.com and pop in your email address to see if it’s featured in a data breach. If it has been then change your password! This doesn’t mean you have been hacked, but it’s certainly possible that if this information is out there you could be.
How to protect your Mac from hackers
macOS is a very secure system, so there’s no need to panic, but if you want to reduce the chances of being compromised then there are a few things to do.
- The first is to only download software from either the Mac App Store or the official websites of manufacturers.
- You should also avoid clicking on links in emails in case they lead you to spoof websites and malware.
- Don’t use USB cables, other cables, or memory sticks, that if you can’t be sure that they are safe.
- When you are browsing the web surf in private or incognito mode.
- If you ever receive a ransomware request or a phishing email do not respond as all this does is confirm that you exist.
- Another is to make sure you download updates to macOS as soon as they become available as they usually include security patches. In fact, you can set up your Mac to automatically download such updates. Turn on Automatic Updates in System Settings > Software Update, click on the i beside Automatic Updates and select all the options. Pre-Ventura, go to System Preferences > Software Update and click beside Automatically keep my Mac up to date pre-Ventura.
- Finally, consider using a dedicated security software package. You’ll find our pick of the current offerings in best Mac antivirus. Right now our top choices are Intego Mac Internet Security, but we also like McAfee Total Protection, and Norton 360 Deluxe.
- You should also consider using a password manager, as this will allow you to have multiple, complicated login details across all your accounts without having to remember them. Here our recommendations are LastPass, 1Password, and NordPass.

Dominik Tomaszewski / Foundry
FAQ
Can Macs get hacked?
It may be rare when compared to Windows, but yes, there have been cases where Macs have been accessed by hackers.
These kinds of attack aren’t likely to affect the general public though, so if you aren’t protecting state secrets or heavily invested in cryptocurrency you are unlikely to fall fowl of such an attack.
What are some examples of Macs being hacked
There are various types of Mac malware that have been discovered ‘in the wild’ on Macs as you can see from our run-through of the various threats affecting macOS: List of Mac viruses, malware and security flaws.
Soon after launch, Malware targeted the M1 Mac – read about Silver Sparrow and the first cases of malware for M1 Macs.
In August 2023 a software developer released details about a flaw in App Management, a security feature introduced in macOS Ventura designed to prevent malicious software modifications and alerting the user in such an instance. The developer had discovered the issue before the release of Ventura in October 2022, but a fix was not immediately issued, so, in August 2023, the developer went public with details of the flaw which meant that apps could bypass the check by App Management. More here.
In December 2023, a group of university researchers alerted Apple to a vulnerability in Apple’s M-series chips that can be exploited to gain access to cryptographic keys. Dubbed “GoFetch,” the vulnerability could be used by an attacker to access a user’s encrypted files.
In April 2024 Apple alerted some users via an email, suggesting that they may have been the target of spyware. “Apple detected that you are being targeted by a mercenary spyware attack that is trying to remotely compromise the iPhone associated with your Apple ID -xxx-,” read the email, as detailed here: Apple warns users in 92 countries of spyware attack.
It’s not always a flaw in Apple’s software that can leave Macs vulnerable. In August 2023 a serious vulnerability that affected Intel processors was highlighted. Affected devices included Intel-powered Macs from 2015 onwards (M-series Macs were all ok). According to researcher Daniel Moghimi: “Downfall attacks target a critical weakness found in billions of modern processors used in personal and cloud computers.” Intel released a patch, but it’s not the first time this has happened. Back in 2018, in a similar case, Meltdown and Spectre attacked vulnerabilities in Intel and ARM processors. That risk was mitigated by updates to the operating system which closed off the areas that were exposed.
Such vulnerabilities, though rare, could allow an attacker root access to your Mac.
What does Apple do about hacks
Apple has gone to great lengths to make it difficult for hackers to gain access to Macs. With the protections offered by Gatekeeper, the Secure Enclave features of the M-series of chips, and the T1 or T2 chip in some Intel-powered Macs, plus Apple’s built-in antivirus XProtect, targeting Macs may well be considered too much effort by hackers. We discuss this in more detail here: How secure is a Mac? and in Do Macs need antivirus software?
However, from time to time security vulnerabilities are detected that could be used by hackers to exploit Macs. These vulnerabilities are sometimes referred to as back doors or as a zero-day vulnerability. When these are identified by security researchers (or friendly hackers) they usually alert Apple to them in the hope that the company will quickly close the vulnerability, quickly – or within zero days – before it is exploited.
Apple encourages researchers to point out vulnerabilities, and when a vulnerability is discovered, Apple is usually quick to fix. Apple has even paid money to those who brought security flaws to its attention. For example, in 2021, Apple paid a student $100,000 after he discovered a dangerous vulnerability relating to Macs and reported it to Apple. The vulnerability, which could enable a hacker to gain control of a Mac user’s camera, was identified by Ryan Pickren in July 2021 and fixed by Apple in macOS Monterey 12.0.1 on October 25, 2021. More information here: Hacker ‘could take over any Apple webcam’.
But there have been cases where Apple has been criticized for being slow to respond to the threat once it’s been identified. For example, researcher Filippo Cavallarin found a Gatekeeper vulnerability in 2019 that he alerted Apple to. Having had no response from Apple within 90 days he went public with details of the vulnerability.
How does Apple protect Macs from hackers
Apple is kept busy patching these security flaws as and when they arise, but it used to be reliant on users to install them. Before Apple launched macOS Ventura in 2022 an update to the operating system was required to get the important security component on a Mac. Since some people delay installing operating system updates this was problematic so Apple changed the way security updates are applied to Macs. These important security updates can now be delivered as background updates that can be automatically installed on a Mac without the user having to do anything – although we recommend you check the following to ensure it is set up on your Mac:
- Open System Settings.
- Choose General.
- Click on the i beside Automatic Updates.
- Make sure that the option to Install Security Responses and system files is selected, even if you choose not to select the others (although we recommend you do).
Now your Mac will check for updates, download the update, and install the update without you needing to do anything.
If you aren’t running a recent version of macOS then Apple won’t be issuing any security updates for you. Apple only issues security updates for the current three versions of macOS, see: How long does Apple support Macs for. For that reason we recommend that you have a Mac that supports at least the version of macOS from two years ago. Currenly only macOS Tahoe, which launched in fall 2025, macOS Sequoia and macOS Sonoma are supported with security updates. Luckily this does mean most Macs from 2018 and later are supported. Read: The latest version of macOS your Mac can run.
Can a Mac camera be hacked?
Once a hacker has access to your Mac there are various ways in which they might try to gain information about you or use the processing power of your Mac for their own purposes. As we mentioned above, in the case of spyware the hacker might attempt to install a keylogger so that it can record what you are typing and look out for your password. The hacker could also attempt to hijack your mic or video camera.
Theoretically, this shouldn’t be possible: since macOS Catalina launched in 2019 Apple has protected Mac users from these types of exploits by ensuring that you have to give your permission before the mic or video camera is used, or before a screen recording can take place. And if your video camera is being used you will always see a green light next to it. However, the example we mentioned above, where Ryan Pickren alerted Apple to a vulnerability that could enable a hacker to gain control of a Mac user’s camera, suggests that Apple’s alert wasn’t enough to stop the camera from being accessed.
There was also a camera-related vulnerability that affected Mac users of the video conferencing service Zoom. In this case, hackers could add users to video calls without them knowing and then activate their webcams but keep the light turned off. This would enable any potential hackers (or law enforcement bodies) to monitor your activities and you wouldn’t have any idea that the camera was watching you. Zoom patched the vulnerability, but only after it became public knowledge when the person who found it reported that the flaw had been left in place for three months after the company had been privately informed of the risk. For more information read: How to stop your Mac webcam being hacked.
Wondering about whether FaceTime is secure? Read Is Apple FaceTime safe?

Dominik Tomaszewski / Foundry
Glossary of terms
We’ll run through the types of hacks that are more pertinent to the hacking of Macs below:
Cryptojacking: This is where someone uses your Mac’s processor and RAM to mine cryptocurrency. If your Mac has slowed right down this could be the culprit.
Spyware: Here hackers attempt to gather sensitive data about you, such as your log in details. They might use key loggers to record what you type and eventually have the information they need to log in to your accounts. In one example, the OSX/OpinionSpy spyware was stealing data from infected Macs and selling it on the dark web.
Ransomware: Some criminals use Ransomware to try and extort money from you. In cases like KeRanger hackers could have encrypted files on Macs and then demand money to unencrypt them. Luckily Security researchers identified KeRanger before it started infecting Macs so it was addressed before it became a serious threat. In April 2023 security researchers warned that a collective known as LockBit was working on ransomware encryptors that work on both Macs using Apple M-series chips and Intel processors.
Botnet: In this case, your computer becomes a remotely operated spam machine. In the case of the Trojan Horse botnet OSX.FlashBack over 600,000 Mac computers.
Proof-of-concept: Sometimes the threat isn’t actually seen in the wild, but is a proof of concept based on a loophole or vulnerability in Apple’s code. While this is less of a threat the concern is that if Apple isn’t quick enough to close the vulnerability it could be utilized by criminals. In one example Google’s Project Zero team designed a proof-of-concept known as Buggy Cos which was able to gain access to parts of macOS thanks to a bug in macOS’ memory manager.
Port exploits: It’s not always the case that the hack is made possible by some sort of malware downloaded onto the Mac. In some cases, Macs have been hacked after something is plugged into a port. It is possible that Macs could be hacked via the USB and by the Thunderbolt port – which is a good reason to always be careful about what you plug into your Mac or leave your Mac unattended. For example, in the checkm8 exploit it could have been possible for hackers to gain access to the T2 chip by plugging in a modified USB-C cable. Similarly, in the case of Thunderspy a serious vulnerability with the Thunderbolt port could have granted a hacker access to a Mac.
Feeling more secure now? Learn even more by reading the helpful tips in How to keep your Mac secure.



